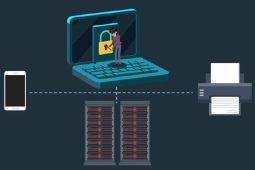
What can I do to protect my students’ work on my device?
Why Do People Fall Victim to Social Engineering Attacks?

Listening to news events where a Qatari Man paid up more than half a million dollars to three Nigerian men posing as the daughter-in-law of a deceased leader, you often wonder how could anyone fall for something like that.
What we fail to realize is that even though we might be the most tech-savvy person, even clicking a harmless link or downloading an attachment that seems to be from a known friend could trap you into a social engineering attack. This is because the perpetrator believes that they can gain your trust and confidence by sending the mail through a familiar person or giving the appearance of an authorized site.
Social engineers who plan these attacks rely on the vulnerabilities of human beings which means that they take advantage of a person’s emotions or state of mind to get their way. They usually monitor the person they plan to fool well in advance so that they can be familiar with them and be confident while interacting to put them at ease.
For example: to gain information on your bank account, a social engineer could create a fake banking email address and use an official tone and banking language. He may even create a sense of urgency suggesting criticality of information for the safety of your finances. This puts you under pressure to give in and share the needed information. If you are not alert you could be easy prey. There have been instances when people have secured educational loans from banks by stealing the identities of bright students.
Recent years have also seen schools and universities under cyber-attack. An academic institution had its Internet technology database hacked and they had to recommend to the staff and students to reset their passwords. Another large university had its personal information records hacked. It could be a phony email pretending to be the Dean of the University asking one of its IT staff to reset his password through the university’s secure confidential site. A less vigilant member of staff could have succumbed to it giving access to the intruder.
There is no place that is 100% secure; be it school, home, or even on the playground, you have to be alert for an attack anywhere. Parents should advise children not to respond to any unknown person who uses their name or narrates tales of them being involved in an accident to take them home. Be it in the physical world or in the online world alertness is the key to preventing such incidents. Online social media sites are a popular hangout for youngsters, be it Facebook, Twitter, or another. They are always eager to be updated with the latest ‘in-thing’. Social Engineers rely on the eager and curious nature of teenagers to engage them in a security breach. They either promise them the latest application download for free in exchange for certain information or pretend to be a friend to compromise their secure information.
As responsible parents, teachers, and students, an awareness and understanding of what goes into a social engineering attack can prevent one from being a victim.
@2x.png)